Getting The VM Started
Starting at Task 1, you will see the green Start Machine button. Click this button to get the VM Started.
Scroll to the top where the banner is. On the right side of the page, you will see the blue Show Split view. Click this blue button.
The page will split, now just wait till the VM loads.
Once the VM loads, click the View in Full Screen icon in the bottom left of the VM.
A new browser tab should open with the VM in it.
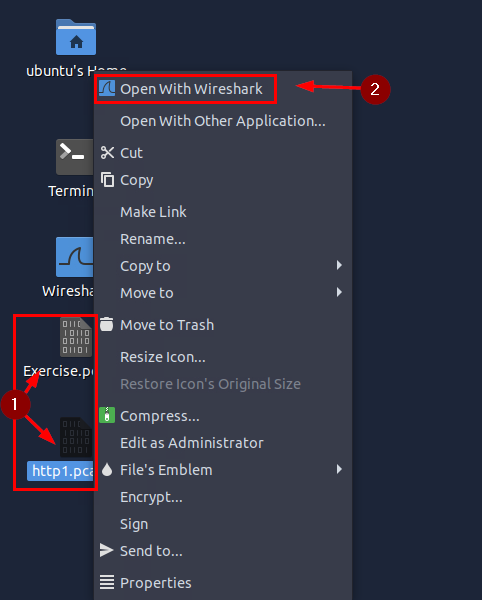
Now depending on what you are doing, if you are following along with the screenshot, use http1.pcapng. If you are answering the questions, use Exercise.pcapng. Whichever you choose, right-click on the file, then on the drop-down menu click the Open With Wireshark.
This will open that file into Wireshark, and you will be ready to go!!
Task 1 Introduction
Wireshark is an open-source, cross-platform network packet analyzer tool capable of sniffing and investigating live traffic and inspecting packet captures (PCAP). It is commonly used as one of the best packet analysis tools. In this room, we will look at the basics of Wireshark and use it to perform fundamental packet analysis.
Note: A VM is attached to this room. You don’t need SSH or RDP; the room provides a “Split View” feature. We suggest completing the Network Fundamentals module before starting working in this room.
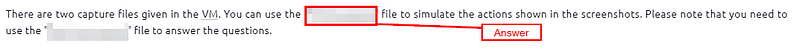
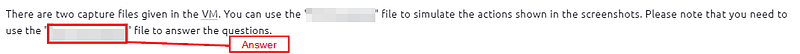
There are two capture files given in the VM. You can use the “http1.pcapng” file to simulate the actions shown in the screenshots. Please note that you need to use the “Exercise.pcapng” file to answer the questions.
Answer the questions below
All the answers can be found above, so I won’t be providing them here.
Which file is used to simulate the screenshots?
The Answer to this question can be found in the last paragraph of the above section. Once you find it, type the answer into the TryHackMe answer field and click submit.
Which file is used to answer the questions?
The Answer to this question can be found in the last paragraph of the above section. Once you find it, type the answer into the TryHackMe answer field and click submit.
Task 2 Tool Overview
Use Cases
Wireshark is one of the most potent traffic analyzer tools available in the wild. There are multiple purposes for its use:
- Detecting and troubleshooting network problems, such as network load failure points and congestion.
- Detecting security anomalies, such as rogue hosts, abnormal port usage, and suspicious traffic.
- Investigating and learning protocol details, such as response codes and payload data.
Note: Wireshark is not an Intrusion Detection System (IDS). It only allows analysts to discover and investigate the packets in depth. It also doesn’t modify packets; it reads them. Hence, detecting any anomaly or network problem highly relies on the analyst’s knowledge and investigation skills.
GUI and Data
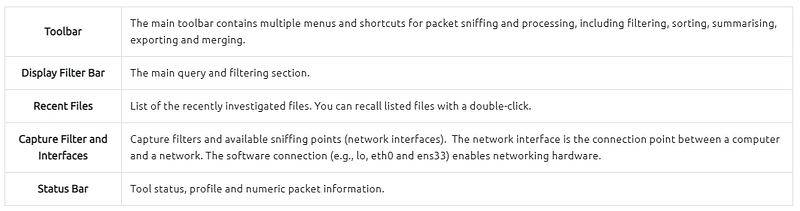
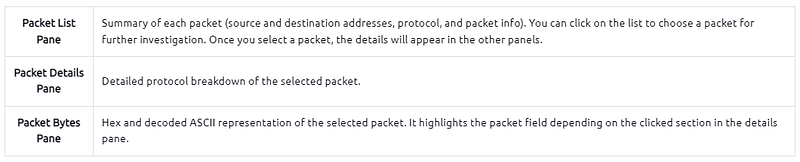
Wireshark GUI opens with a single all-in-one page, which helps users investigate the traffic in multiple ways. At first glance, five sections stand out.
Use Cases
Wireshark is one of the most potent traffic analyzer tools available in the wild. There are multiple purposes for its use:
- Detecting and troubleshooting network problems, such as network load failure points and congestion.
- Detecting security anomalies, such as rogue hosts, abnormal port usage, and suspicious traffic.
- Investigating and learning protocol details, such as response codes and payload data.
Note: Wireshark is not an Intrusion Detection System (IDS). It only allows analysts to discover and investigate the packets in depth. It also doesn’t modify packets; it reads them. Hence, detecting any anomaly or network problem highly relies on the analyst’s knowledge and investigation skills.
GUI and Data
Wireshark GUI opens with a single all-in-one page, which helps users investigate the traffic in multiple ways. At first glance, five sections stand out.
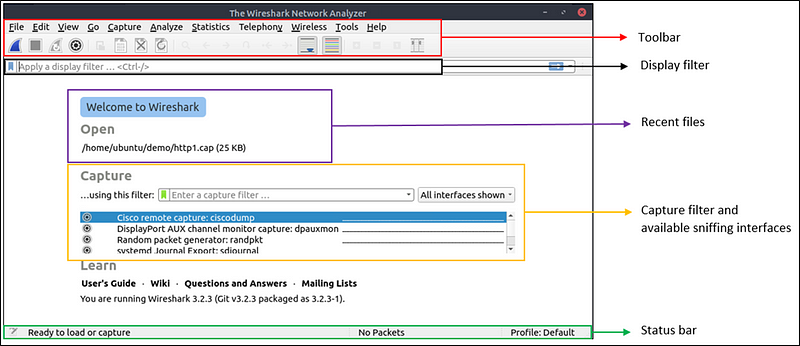
The below picture shows Wireshark’s main window. The sections explained in the table are highlighted. Now open the Wireshark and go through the walkthrough.
Loading PCAP Files
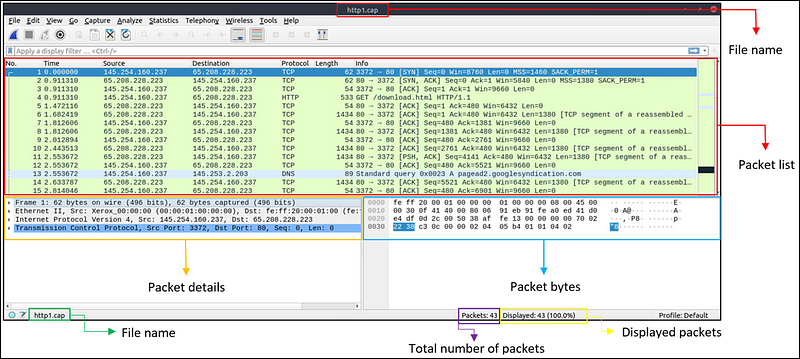
The above picture shows Wireshark’s empty interface. The only available information is the recently processed “http1.cap” file. Let’s load that file and see Wireshark’s detailed packet presentation. Note that you can also use the “File” menu, dragging and dropping the file, or double-clicking on the file to load a pcap.
Now, we can see the processed filename, detailed number of packets and packet details. Packet details are shown in three different panes, which allow us to discover them in different formats.
Coloring Packets
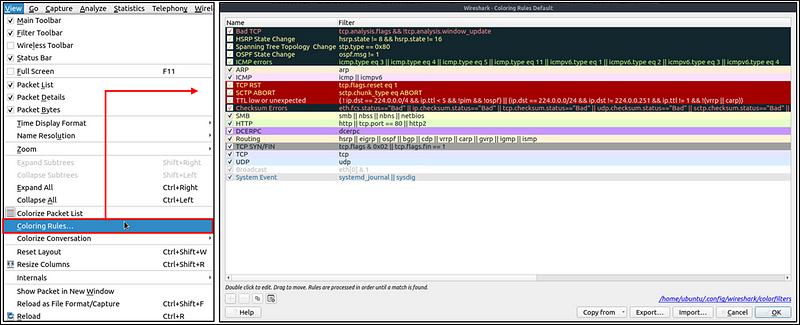
Along with quick packet information, Wireshark also color packets in order of different conditions and the protocol to spot anomalies and protocols in captures quickly (this explains why almost everything is green in the given screenshots). This glance at packet information can help track down exactly what you’re looking for during analysis. You can create custom color rules to spot events of interest by using display filters, and we will cover them in the next room. Now let’s focus on the defaults and understand how to view and use the represented data details.
Wireshark has two types of packet coloring methods: temporary rules that are only available during a program session and permanent rules that are saved under the preference file (profile) and available for the next program session. You can use the “right-click menu” or “View → Coloring Rules” menu to create permanent coloring rules. The “Colorize Packet List” menu activates/deactivates the coloring rules. Temporary packet coloring is done with the “right-click menu” or “View → Conversation Filter” menu, which is covered in TASK-5.
The default permanent colouring is shown below.
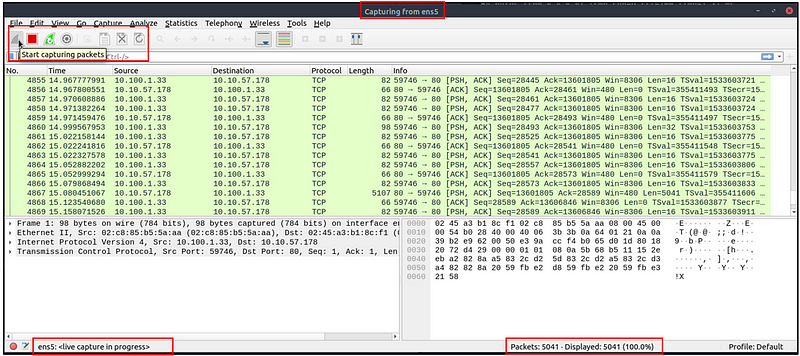
Traffic Sniffing
You can use the blue “shark button” to start network sniffing (capturing traffic), the red button will stop the sniffing, and the green button will restart the sniffing process. The status bar will also provide the used sniffing interface and the number of collected packets.
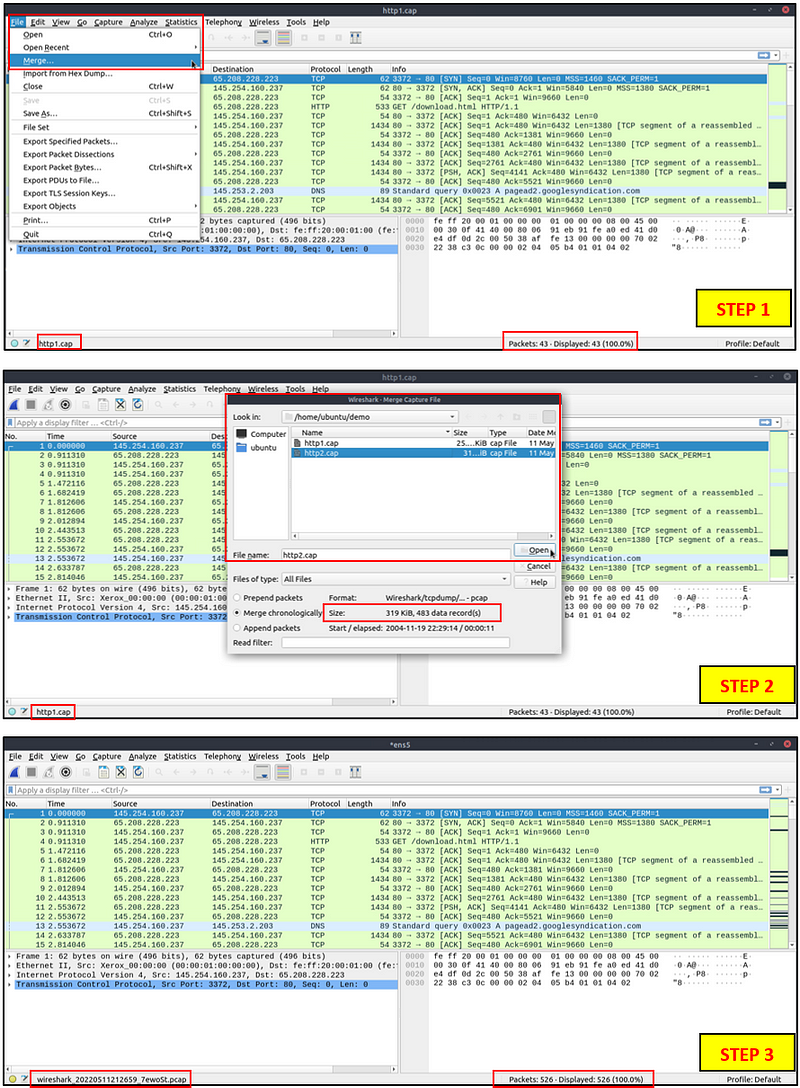
Merge PCAP Files
Wireshark can combine two pcap files into one single file. You can use the “File → Merge” menu path to merge a pcap with the processed one. When you choose the second file, Wireshark will show the total number of packets in the selected file. Once you click “open”, it will merge the existing pcap file with the chosen one and create a new pcap file. Note that you need to save the “merged” pcap file before working on it.
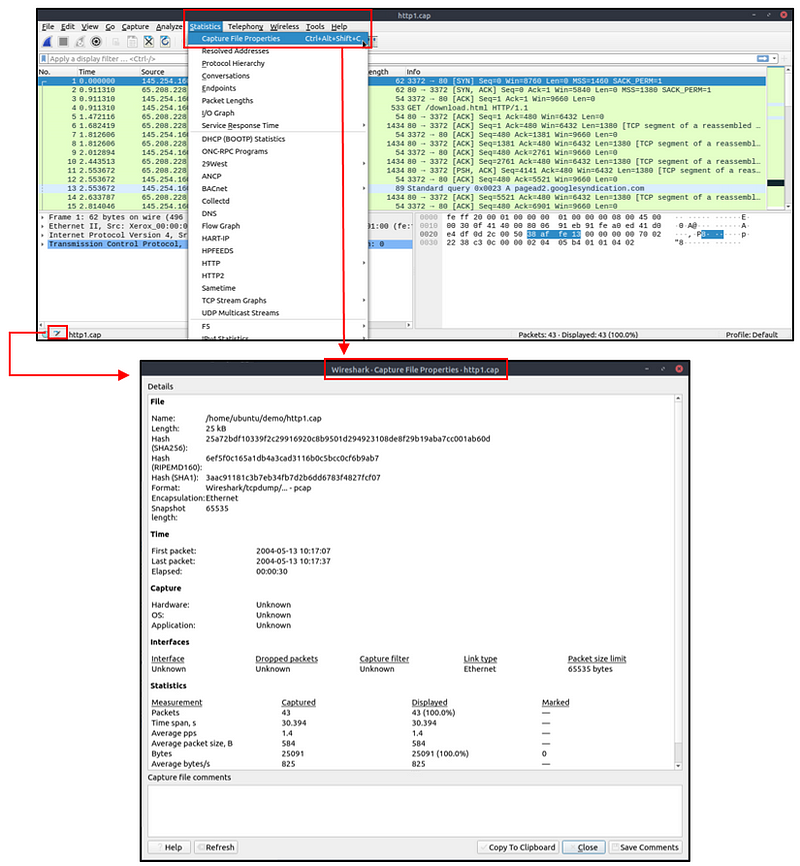
View File Details
Knowing the file details is helpful. Especially when working with multiple pcap files, sometimes you will need to know and recall the file details (File hash, capture time, capture file comments, interface and statistics) to identify the file, classify and prioritize it. You can view the details by following “Statistics → Capture File Properties” or by clicking the “pcap icon located on the left bottom” of the window.
Answer the questions below
Use the “Exercise.pcapng” file to answer the questions.
If you haven’t already, scroll to the top of this write-up and follow the steps it takes to load the pcap file into Wireshark. Once you have done this, proceed to the questions.
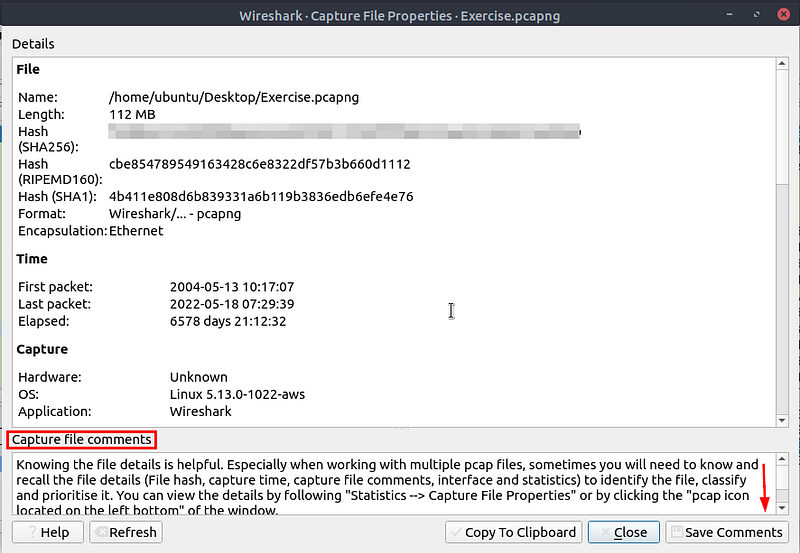
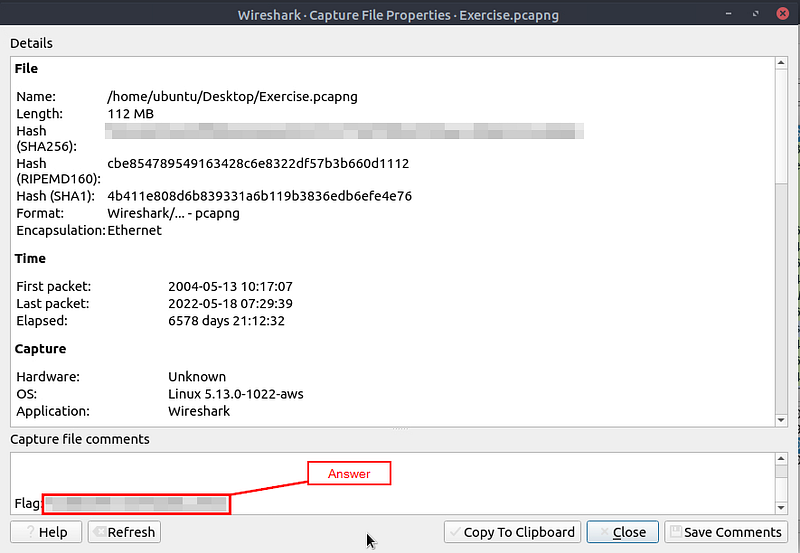
Read the “capture file comments”. What is the flag?
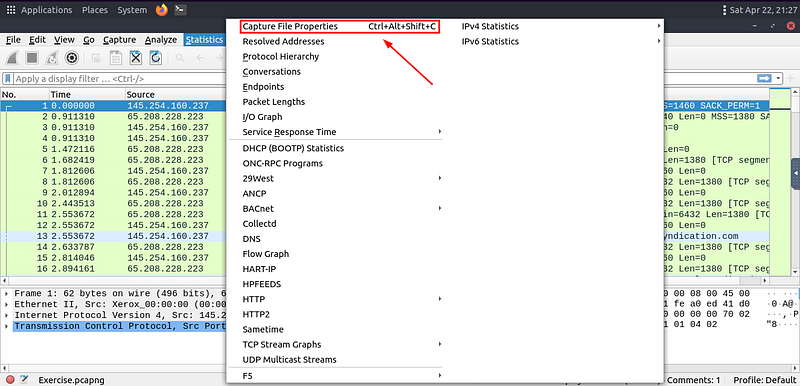
Go to the toolbar at the top of Wireshark, and look for Statistics.
Either click on Statistics or press the letter S to have the drop-down appear. On the drop-down menu, click Capture File Properties.
The Wireshark — Capture File Properties window will pop up. Look at the bottom of this window for the Capture File Comments section. Once you see it, scroll to the bottom.
When you reach the bottom of this section, you will see Flag: followed by the flag. Highlight the flag, then copy (ctrl +c) then paste (ctrl +v) the flag in the TryHackMe answer field and click submit.
Answer: TryHackMe_Wireshark_Demo
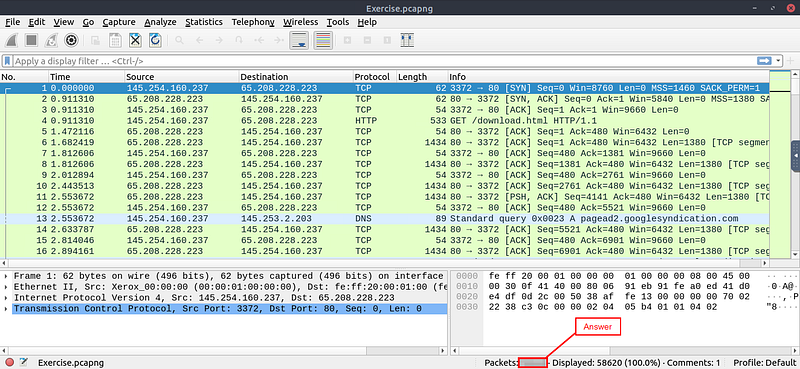
What is the total number of packets?
Starting back on the main page of Wireshark, look at the bottom info bar. Look for the word Packets:, the answer will be to the right of this word. Highlight the number, then copy (ctrl +c) then paste (ctrl +v) the flag in the TryHackMe answer field and click submit.
Answer: 58620
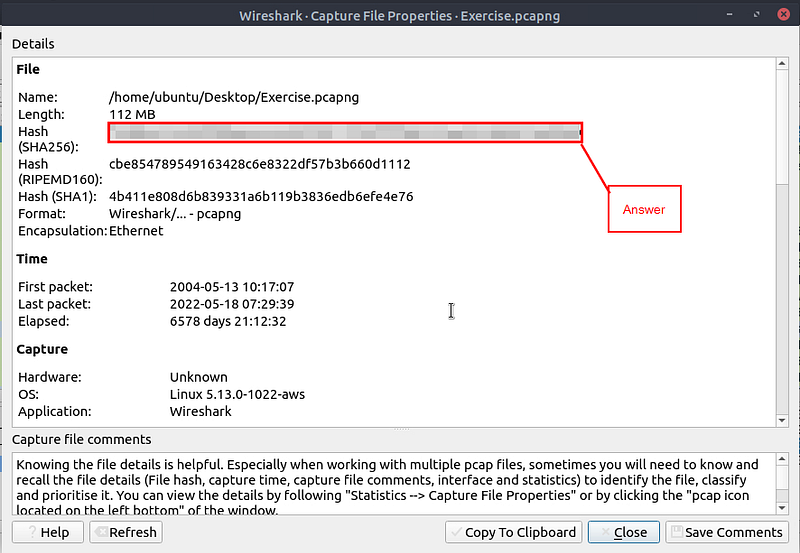
What is the SHA256 hash value of the capture file?
Go to the toolbar at the top of Wireshark, and look for Statistics.
Either click on Statistics or press the letter S to have the drop-down appear. On the drop-down menu, click Capture File Properties.
The Wireshark — Capture File Properties window will pop up. Look in the Details section for Hash(SHA256):, When you find it, you will see a long string of alphanumeric characters. This is the answer, highlight the hash, then copy (ctrl +c) then paste (ctrl +v) the flag in the TryHackMe answer field and click submit.
Answer: f446de335565fb0b0ee5e5a3266703c778b2f3dfad7efeaeccb2da5641a6d6eb
You have finished these tasks and can now move on to Task 3 Packet Dissection & Task 4 Packet Navigation.