TryHackMe Wireshark:Traffic Analysis — Task 9 Bonus: Hunt Cleartext Credentials!, Task 10 Bonus: Actionable Results!, and Task 11 Conclusion
If you haven’t done tasks 7 and 8 yet, here is the link to my write-up of them: Task 7 Cleartext Protocol Analysis: HTTP & Task 8 Encrypted Protocol Analysis: Decrypting HTTPS
Getting the VM Started
Starting at Task 1, you will see the green Start Machine button. Click this button to get the VM Started.
Scroll to the top where the banner is. On the right side of the page, you will see the blue Show Split view. Click this blue button.
The page will split, now just wait till the VM loads.
Once the VM loads, click the View in Full Screen icon in the bottom left of the VM.
A new browser tab should open with the VM in it.
Double-Click on the e_xercise-pcap_ folder to open it.
While folder opens, head back to the THM Task Tab. At the bottom of the VM you will see a minus ( — ), this represents Exit Split View. Click the — to allow the THM task to incapsilate the entire window. This won’t close out of your VM instance, it will just be on the other tab.
Heading back to the browser tab that the VM is in. The folder should be open. Inside this folder will be other folders containing the files needed for the tasks ahead. The folders are named accordingly to the task they are associated with.
Task 9 Bonus: Hunt Cleartext Credentials!
Bonus: Hunt Cleartext Credentials!
Up to here, we discussed how to inspect the packets for specific conditions and spot anomalies. As mentioned in the first room, Wireshark is not an IDS, but it provides suggestions for some cases under the expert info. However, sometimes anomalies replicate the legitimate traffic, so the detection becomes harder. For example, in a cleartext credential hunting case, it is not easy to spot the multiple credential inputs and decide if there is a brute-force attack or if it is a standard user who mistyped their credentials.
As everything is presented at the packet level, it is hard to spot the multiple username/password entries at first glance. The detection time will decrease when an analyst can view the credential entries as a list. Wireshark has such a feature to help analysts who want to hunt cleartext credential entries.
Some Wireshark dissectors (FTP, HTTP, IMAP, pop and SMTP) are programmed to extract cleartext passwords from the capture file. You can view detected credentials using the “Tools → Credentials” menu. This feature works only after specific versions of Wireshark (v3.1 and later). Since the feature works only with particular protocols, it is suggested to have manual checks and not entirely rely on this feature to decide if there is a cleartext credential in the traffic.
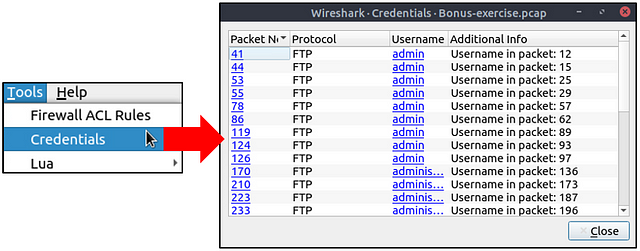
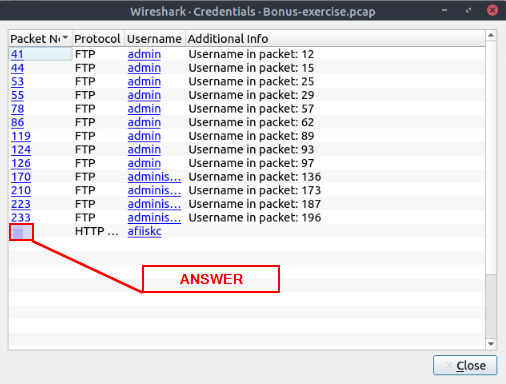
Once you use the feature, it will open a new window and provide detected credentials. It will show the packet number, protocol, username and additional information. This window is clickable; clicking on the packet number will select the packet containing the password, and clicking on the username will select the packet containing the username info. The additional part prompts the packet number that contains the username.
Answer the questions below
Use the “Desktop/exercise-pcaps/bonus/Bonus-exercise.pcap” file.
Inside the exercise-pcaps folder, double-click on the bonus folder.
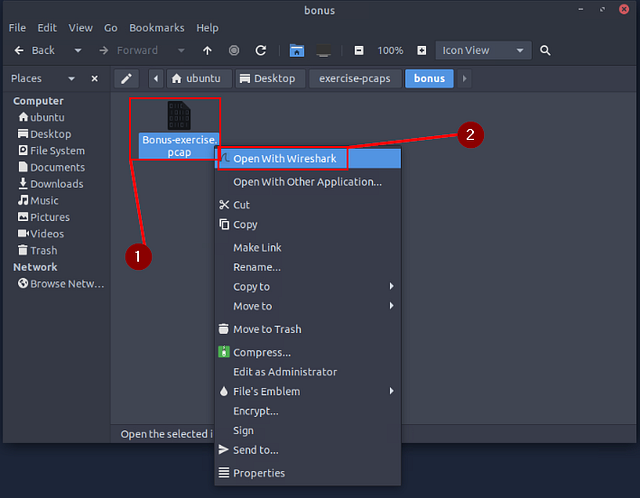
Inside the bonus folder you will see the Bonus-exercise.pcap file. Right-click on it, then choose Open With Wireshark from the drop-down menu.
What is the packet number of the credentials using “HTTP Basic Auth”?
Click on the Tools drop-down menu at the top of the Wireshark window. From the drop-down, click on Credentials.
The Wireshark Credentials window will pop up. Looking through the Protocols, we can see one HTTP Packet. Looking at the Packet Number to the left we have our answer. Type the Packet Number into the TryHackMe answer field, then click Submit.
Answer: 237
What is the packet number where “empty password” was submitted?
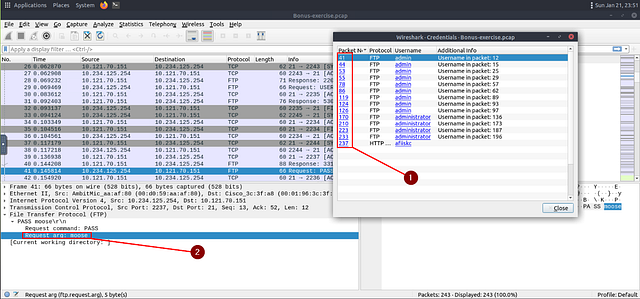
Time to do some investigating! In the Wireshark Credentials Window, click on the Packet Number. You will see that the Packet Details change to the Packet Number you clicked on. Looking at the Request arg: will show you the password that was used. Now click down through the Packet Numbers till you don’t see Request arg:, this means that no password was submitted. Once you find this Packet, you have found the Packet Number that is the answer. Type this answer into the TryHackMe answer field, then click the Submit button.
Answer: 170
Task 10 Bonus: Actionable Results!
Bonus: Actionable Results!
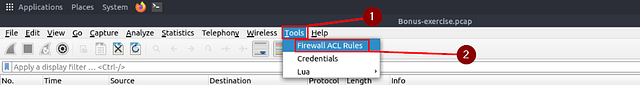
You have investigated the traffic, detected anomalies and created notes for further investigation. What is next? Not every case investigation is carried out by a crowd team. As a security analyst, there will be some cases you need to spot the anomaly, identify the source and take action. Wireshark is not all about packet details; it can help you to create firewall rules ready to implement with a couple of clicks. You can create firewall rules by using the “Tools → Firewall ACL Rules” menu. Once you use this feature, it will open a new window and provide a combination of rules (IP, port and MAC address-based) for different purposes. Note that these rules are generated for implementation on an outside firewall interface.
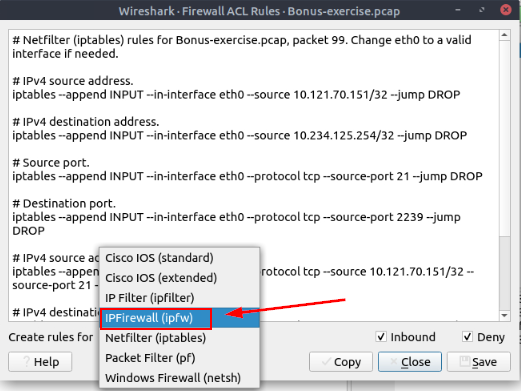
Currently, Wireshark can create rules for:
- Netfilter (iptables)
- Cisco IOS (standard/extended)
- IP Filter (ipfilter)
- IPFirewall (ipfw)
- Packet filter (pf)
- Windows Firewall (netsh new/old format)
Answer the questions below
Use the “Desktop/exercise-pcaps/bonus/Bonus-exercise.pcap” file.
You will use the same Bonus-exercise.pcap file you opened in the previous Task.
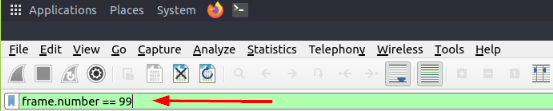
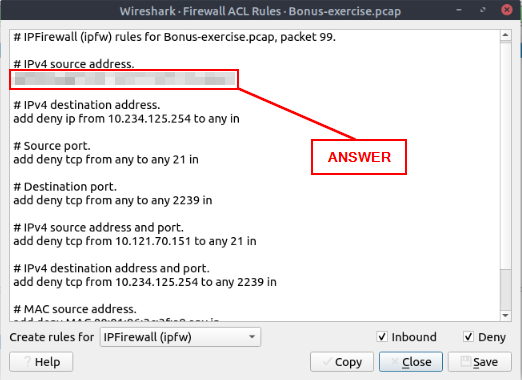
Select packet number 99. Create a rule for “IPFirewall (ipfw)”. What is the rule for “denying source IPv4 address”?
Let’s start by filtering for only Packet 99. Using the frame.number filter we used before, adding == 99. So that the filter is frame.number == 99, then press enter to run the filter.
Click on the Tools drop-down menu at the top of the Wireshark window. From the drop-down, click on Firewall ACL Rules.
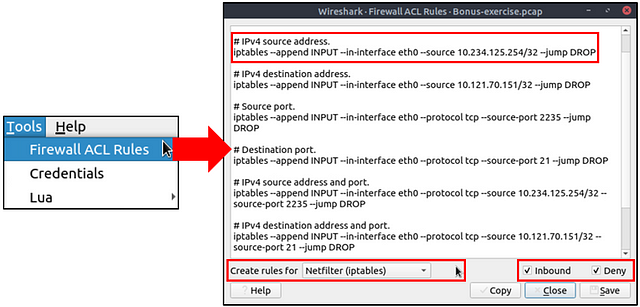
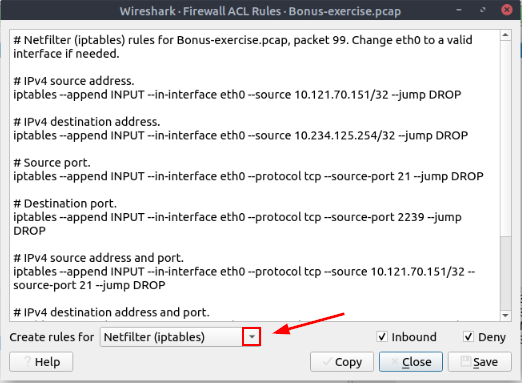
The Wireshark Firewall ACL Rules window will pop up. At the bottom of the window we can see Create Rules For with a drop-down menu to the right. Click the down carot to expand this menu.
The drop-down will expand. Look for IPFirewall (ipfw), once you find it, click on it. This will select it.
The IPFirewall (ipfw) rules will be loaded in the window now. As we can see, the rule for denying IPv4 source address is at the top of the list. Highlight the rule and copy (ctrl + c), then paste it in the TryHackMe answer field. Then click Submit.
Answer: add deny ip from 10.121.70.151 to any in
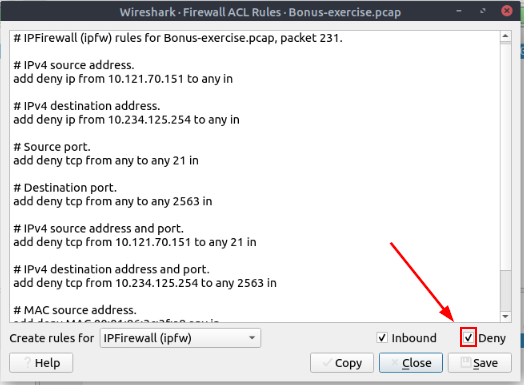
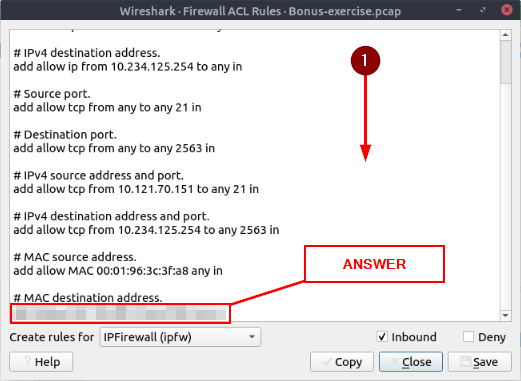
Select packet number 231. Create “IPFirewall” rules. What is the rule for “allowing destination MAC address”?
Close out the Wireshark Firewall ACL Rules window using the Close button in the bottom right of the window.
Now change the Frame Number from 99 to 231. So that the filter will look like frame.number == 231, then press enter to run it.
Click on the Tools drop-down menu at the top of the Wireshark window. From the drop-down, click on Firewall ACL Rules.
The Wireshark Firewall ACL Rules window will pop up. At the bottom of the window we can see Create Rules For with a drop-down menu to the right. Click the down carot to expand this menu.
The drop-down will expand. Look for IPFirewall (ipfw), once you find it, click on it. This will select it.
One final thing we need to do is uncheck the deny box in the bottom right of the window. This will change the rules to be allow instead of deny.
Now scroll down till you see MAC destination address. Once you spot it, highlight and copy (ctrl + c) the rule. Then paste (ctrl + v) the answer into the TryHackMe answer field, then click Submit.
Answer: add allow MAC 00:d0:59:aa:af:80 any in
Task 11 Conclusion
Congratulations! You just finished the “Wireshark: The Traffic Analysis” room.
In this room, we covered how to use the Wireshark to detect anomalies and investigate events of interest at the packet level. Now, we invite you to complete the Wireshark challenge room: Carnage, Warzone 1 and Warzone 2.
Wireshark is a good tool for starting a network security investigation. However, it is not enough to stop the threats. A security analyst should have IDS/IPS knowledge and extended tool skills to detect and prevent anomalies and threats. As the attacks are getting more sophisticated consistently, the use of multiple tools and detection strategies becomes a requirement. The following rooms will help you step forward in network traffic analysis and anomaly/threat detection.